Welcome to the Zimbabwe Cyber Security Information,Training & Reporting Platform
Report a cyberthreat
cyber@ictministry.gov.zw
What is a cyber threat?
A cyber threat is a malicious act — or just the possibility of one — that seeks to damage or steal data, or to otherwise disrupt computer networks and systems. Common cyber threats include computer viruses, software vulnerabilities, distributed denial of service attacks (DDoS), and social engineering techniques, such as phishing. Even “offline” events like natural disasters can be considered a cyber threat, as they put systems and data at risk.
Cyber threats may come from a variety of sources, including:
- Criminal gangs
- Nation-states
- Corporate spies
- Disgruntled insiders
- Individual hackers
No matter the source, cyber threats are a massive hazard. They threaten not only business health and operations, but even our daily life in this increasingly-digital world. And with AI and automation making cyberattacks easier to carry out, effective cyber protection is critical.
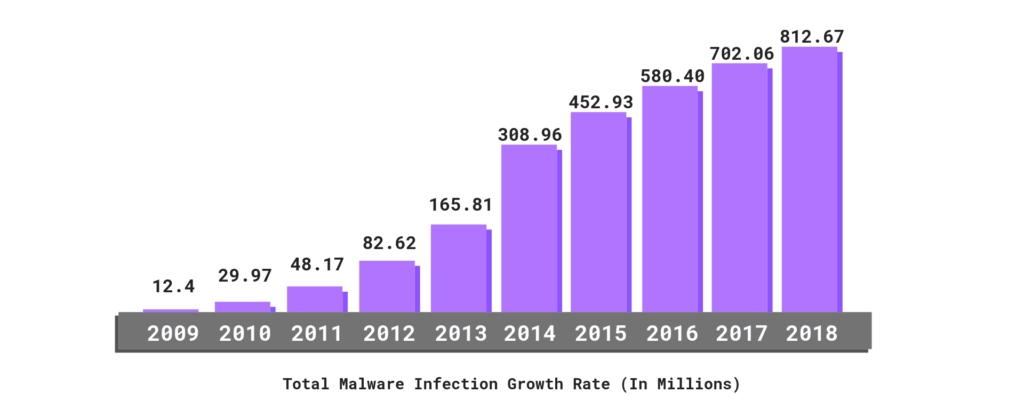
Malware Statistics
Cyber Threats



